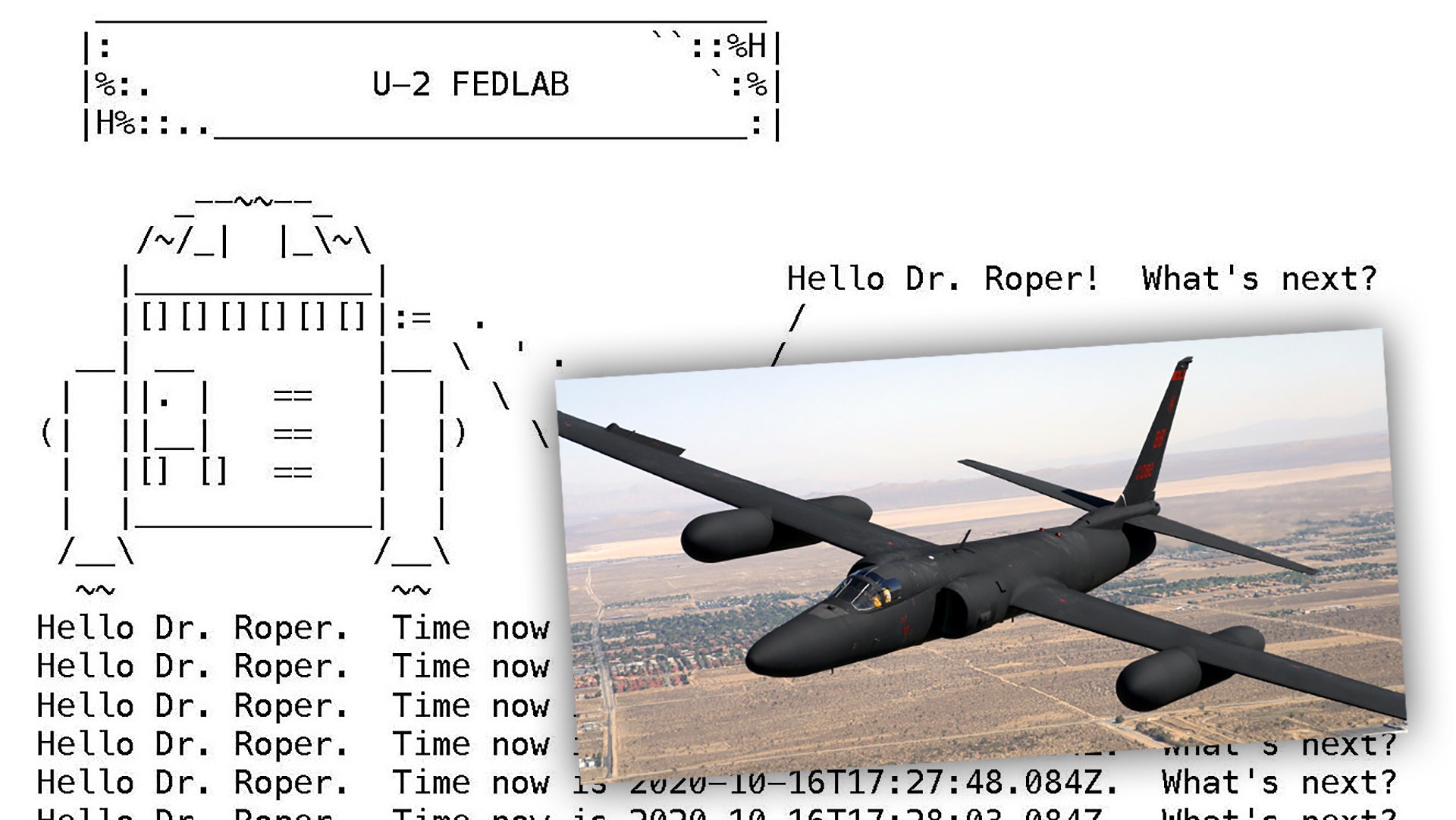
Will Roper, the Assistant Secretary of the Air Force for Acquisition, Technology, and Logistics, has offered new details about how the Air Force successfully made changes to the software onboard a U-2S Dragon Lady spy plane in flight for the first time ever. The first update the plane’s systems received was to add code to help track future changes, which produced a log that also includes a depiction of the iconic Star Wars droid R2-D2 saying “Hello Dr. Roper! What’s next?”
Sci-fi references notwithstanding, this achievement, a first-of-its-kind milestone for the U.S. military on any type of aircraft, at least publicly, is a big deal and could have game-changing impacts on aerial operations in the future, including with regards to intelligence, surveillance, and reconnaissance activities and electronic warfare. The system apparently quickly got an answer to the “what’s next?” question as well, when a second update brought “improved automatic target recognition algorithms” to the U-2S, according to Roper.
Roper Tweeted out details about the patches, as well as a screenshot of the changelog file, on Oct. 19, 2020. The day before he had announced that the updates had occurred, but had not said what they consisted of at that time. He also recently took a flight himself in a two-seat TU-2S trainer, underscoring this recent focus on the iconic spy plane, the initial versions of which first began flying under the auspices of the Central Intelligence Agency (CIA) in 1956.
On Oct. 6, the Air Force had previously revealed that a U-2S from the 9th Reconnaissance Wing at Beale Air Force Base in California had flown a training mission carrying new software, called Kubernetes. This “open-source container-orchestration system,” which Google originally developed and that the Cloud Native Computing Foundation now maintains, is designed to support the automated installation, modification, and updating of applications on a computer. The recent in-flight updates to the Dragon Lady were done through Kubernetes and were conducted with the help of the U-2 Federal Laboratory.
“The successful combination of the U-2’s legacy computer system with the modern Kubernetes software was a critical milestone for the development of software containerization on existing Air Force weapon systems,” Nicolas Chaillan, the Air Force Chief Software Officer, said after that milestone was achieved.
“This is a milestone achievement that paves the way for rapid experimentation as we continuously work to bring the future faster and increase battlespace awareness for our Airmen,” Air Force Colonel Heather Fox, head of the 9th Reconnaissance Wing, added in her own statement. “The integration of Kubernetes onto the U-2 capitalizes on the aircraft’s high altitude line of sight and makes it even more survivable in a contested environment. We look forward to working with other platforms across the DoD to export this incredible capability.”

Being able to update software on devices remotely may not seem like a huge deal to people who regularly get prompted to download patches on their smartphones and personal computers. However, the ability to send new code to military aircraft in flight that could make improvements to mission and flight systems is a far more complex and potentially risky proposition. If something goes wrong, key software on the plane may no longer work, preventing it from completing its mission or worse.
If the process works and works reliably, it could open-up all-new possibilities. The second update that Roper says this particular U-2S received is a perfect example of this. Automated target recognition, whether its spotting objects of interest on radar, or visually or detecting notable electronic emissions, relies heavily on an existing information library of signatures to compare against.
Did an adversary just field a previously unseen major weapon? Are they using a heretofore unknown radar or communications system? A targeting system may not be able to automatically spot them until it gets an update, which, traditionally, would have to occur on the ground. What the Air Force is looking at the possibility of doing now is pushing that new information straight to aircraft in flight as soon as it’s available, potentially while they’re actually on missions, instead of having to wait for a good time to install these patches back at base. This would allow for actionable intelligence to being leveraged in real-time, maximizing the capabilities of the platform when they are needed most.
This doesn’t just apply to targeting systems, either. In-flight software updating via something like Kubernetes will be essential for realizing something referred to as Cognitive Electronic Warfare. You can read more about this concept in detail in this past War Zone piece.
As I previously wrote:
“At its most basic, this concept revolves around the idea of being able to detect and categorize the signals that an opponent is using, for whatever purpose, and then use machine learning and artificial intelligence algorithms to help further automate the process of developing countermeasures and counter-countermeasures. A computer system, especially one with an ever-growing library of electronic signature data collected from a wide array of sources, could parse through that information much faster than a human, or even a team of humans depending on the volume of available intelligence, rapidly identifying items of interest for further analysis and exploitation. It may even be able to start doing some of that follow-on work by itself after isolating the important data.”
…
“…Cognitive EW capabilities could be placed in traditional intelligence processing centers to automate and otherwise help speed up the analysis of new electronic signatures, as well as the creation of new electronic warfare systems or the improvement of existing ones. The increasing use of open-architecture and modular systems that allow for the rapid integration of additional and upgraded capabilities for various pieces of equipment, as well as the introduction of advanced high-bandwidth, long-range communications and data-sharing networks, will make it easier and easier to get those updates to assets in the field on short notice.”
With all this in mind, being able to tweak the algorithms in artificial intelligence-driven systems inside aircraft, including autonomous unmanned aircraft, literally on the fly, could have even further ranging impacts on future U.S. military aerial combat operations. For example, it could be possible eventually to alter how a fully-autonomous unmanned combat air vehicle (UCAV) flies and fights on very short notice in response to the appearance of new enemy air defenses and other systems, as well as changes to their tactics, techniques, and procedures.

There’s no reason, really, why this would have to be limited to aerial operations, necessarily, either. Naval and ground forces, which operate increasingly computerized and networked systems, as well as more and more unmanned platforms, could see the same kind of benefits from this kind of reliable, long-range, on-demand software updating capability.
From the enemy’s perspective, this all presents the prospect of an opponent that is capable of adapting much faster and more accurately than before and is capable of not only developing, but also implementing, highly-tailored counter-countermeasures very quickly.
It’s important to note that the Kubernetes-enabled systems on this one particular U-2S used in these recent tests represent a capability that is still very much in the experimental phase. At the same time, the potential benefits are significant and obvious and the Air Force is clearly committed to see what else this new software and the ability to remotely update systems offers for the Dragon Lady, as well as other platforms.
There will also be a need for robust and secure networks to help transfer all this information. The Air Force is already in the midst of a separate, broader effort to make revolutionary changes to its communications and data-sharing capabilities, as well, as part of the Advanced Battle Management System (ABMS) program. A joint-service ABMS demonstration earlier this year had a number of other very notable components, which you can read about more in the War Zone‘s previous coverage of that event.
All told, the real answer to the change log’s “what’s next?” prompt seems to be “a lot.”
Contact the author: joe@thedrive.com