A White House national security memorandum signed today makes similar recommendations to those found in a Cybersecurity and Infrastructure Security Agency (CISA) memo published yesterday in which the agency stated that recent malware attacks in Ukraine highlight the potential for “widespread damage to critical infrastructure” here in the United States. The CISA memo offers a series of recommended measures that could help detect cyberattacks and reduce possible damage and lists two specific malware threats that have been used previously, NotPetya and the WannaCry ransomware, as examples of just how damaging these attacks can be.
While the CISA memo is aimed broadly at any and all organizations within the United States, the White House’s national security memorandum is focused more specifically on the cybersecurity requirements for national security systems and requires agencies to harden classified networks. The publication of both of these documents this week closely follows a series of cyberattacks in Ukraine suspected of being conducted by Russia and underscores that these same types of attacks could also threaten American systems.
The White House’s memorandum released today builds on a previous Executive Order signed last year aimed at bolstering the cybersecurity of federal government networks. The memorandum outlines a series of requirements and tasks for securing national security systems, including timelines and specifics on how to implement last year’s Executive Order through basic, low-level cybersecurity measures like multifactor authentication, encryption, cloud technologies, and endpoint detection services. The memorandum also requires agencies to report cyber incidents to the National Security Agency (NSA), authorizes the NSA “to take specific actions against known or suspected cybersecurity threats and vulnerabilities,” and requires that agencies strengthen the security of national security systems that have access to classified networks.
National security systems are defined by U.S. code as “any information system (including any telecommunications system) used or operated by an agency or by a contractor of an agency, or other organization on behalf of an agency” involved with intelligence activities, cryptologic activities related to national security, the command and control of military forces, equipment integral to weapons systems, or that is “critical to the direct fulfillment of military or intelligence missions.” There are also a number of classified activities or systems covered by the definition.

To better defend against the potential threats posed by the types of cyberattacks seen in Ukraine recently, CISA recommends that senior leaders at “every organization in the United States” take immediate action to reduce the likelihood of damaging cyberattacks, detect any potential intrusions, ensure they are prepared to respond if an intrusion occurs, and “maximize the organization’s resilience to a destructive cyber incident.”

Microsoft released a blog post this week stating the specific threats it is tracking related to the Ukraine cyberattacks are “destructive and designed to render targeted devices inoperable rather than to obtain a ransom” and “represent an elevated risk to any government agency, non-profit or enterprise located or with systems in Ukraine.” The software giant believes these attacks are related to the recently-discovered malware family known as “WhisperGate.”
While the perpetrators of these attacks remain unknown, there have been a number of claims made that they originate from Russia. Earlier this week, the Ukrainian digital transformation ministry accused Moscow of “continuing to wage a hybrid war” by conducting cyberattacks on Ukrainian government websites and that “all the evidence points to Russia.” Ukrainian foreign ministry spokesman Oleg Nikilenko tweeted on January 14 that while the investigation is still ongoing, the Ukrainian government has found evidence that “hacker groups associated with the Russian secret services” are behind the attacks.
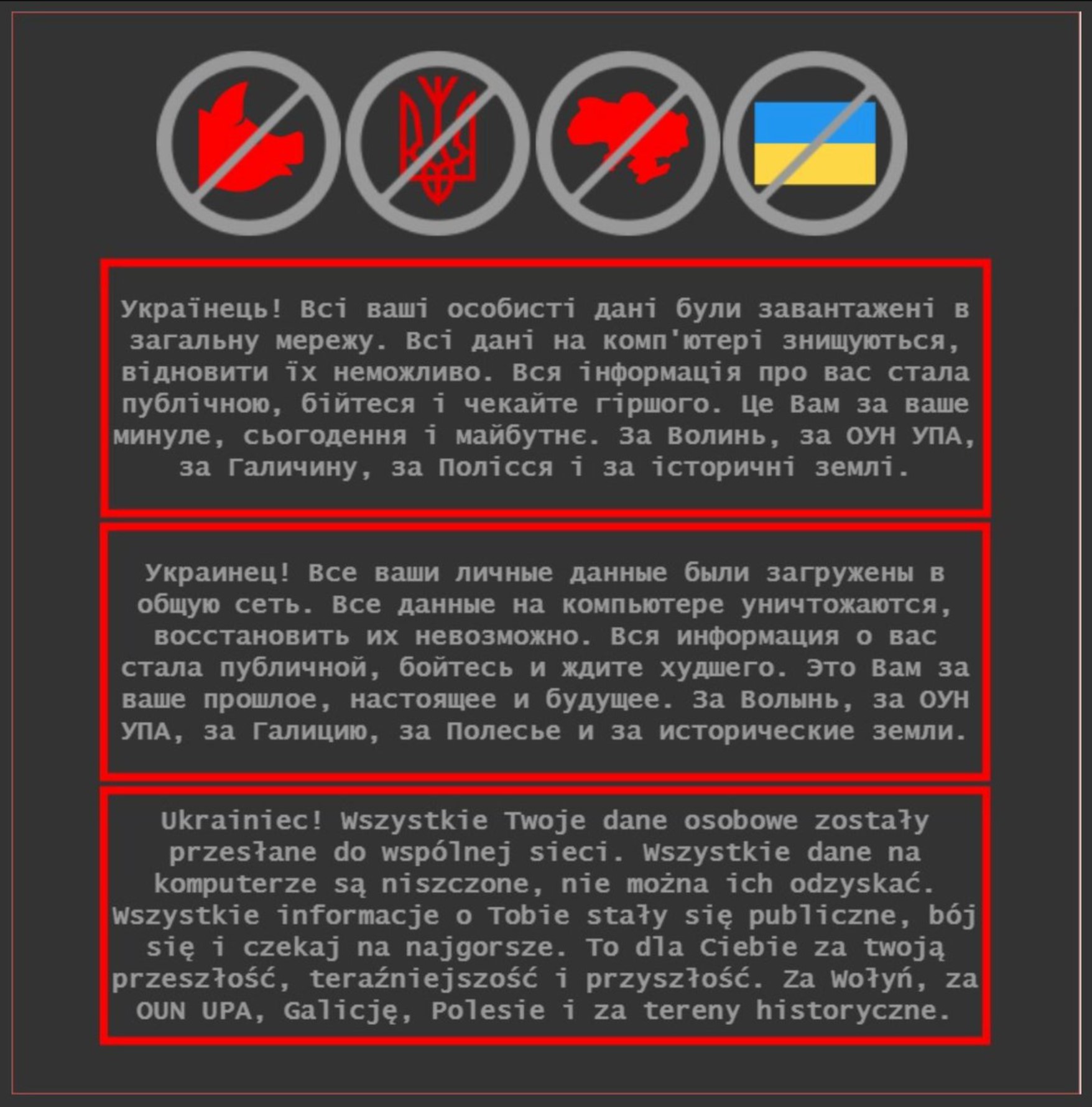
Ukrainian security services say the attacks targeted over 70 Ukrainian government websites, managing to shut at least ten of them down, replacing them with an ominous message that threatened readers that their private information had been hacked and to “be afraid and expect worse.”
The Ukrainian National Cyber Security Coordination Center has named the recent attacks “Operation Bleeding Bear,” and notes that some of the malware identified appears to be similar to other malware used in widespread attacks that occurred in 2017 that hit Ukraine harder than any other nation. Another cyberattack in 2015, suspected to have originated from Russian hacking groups with some level of affiliation with the Russian government, took out a large section of the Ukrainian power grid and saw a quarter-million Ukrainians lose electricity and heat in the dead of winter.
While many believe these attacks likely originated from Russia, Russian presidential spokesman Dmitry Peskov has claimed that the country was not involved at all with these recent cyberattacks. “We have heard accusations against Russia, that Russia is standing behind. But […] not a proof was presented. We consider it a continuation of [other unproven] accusations of Russia,” Peskov said in a recent interview. “We are nearly accustomed to the fact that Ukrainians are blaming everything on Russia, even their bad weather,” he added. Russian President Vladimir Putin has made remarks in the past insinuating that “patriotic” Russians working on their own have been responsible for other cyberattacks targeting the 2016 presidential election.
Meanwhile, an unnamed Ukrainian government official told BuzzFeed News this week that it’s “pretty obvious” Russia was behind the attacks because “hardly anyone else has the motive for such actions.”
The warnings issued by CISA and the White House this week come as other nations such as Poland, which shares a border with Ukraine, have raised their cybersecurity terror threat levels in response to the recent cyberattacks. The Department of Defense has been activating additional cyber units in recent years as these types of cyberattacks against critical infrastructure have become more common and widespread. While the current administration has designated cybersecurity as a high-level priority both at home and internationally, the memoranda issued this week underscore just how vulnerable many critical networks remain.
Contact the author: Brett@TheDrive.com
