When you hear a report about an American counter-terrorism operation, especially one that results in the death or capture of some apparently notable militant in a hot spot around the world, you’ll often hear about how important intelligence was in tracking them down. What you won’t hear much about is exactly what this “intelligence driven” process necessarily entails in any detail. The War Zone has now obtained a document through the Freedom of Information Act that gives a more in depth look at how U.S. special operators are becoming combat detectives, gathering vacuuming up forensic details during missions that could lead them to their next target.
Though it’s just one piece of the intelligence puzzle, so-called “identity intelligence,” or I2, has become an essential part of the action cycle, which broadly involves gathering information, tracking individual terrorists, neutralizing them, and then repeating the process with any new data obtained during those raids. U.S. Special Operations Command (SOCOM) has codified these concepts what it officially calls Directive 525-40, Identity Intelligence. Thanks to the FOIA, we received what appears to be the most recent edition of this document, which is dated April 7, 2017. This replaced a previous version the Pentagon’s top special operations command had published four years earlier.
That special operations forces “will conduct more multinational, intelligence driven, I2 Ops supporting the range of military operations,” is the guide’s number one assumption. “I2 Ops … deny anonymity to the adversary, and protect U.S. and allied assets, facilities, and forces.”
In short, identity intelligence can scoop up information with an eye toward identifying a particular enemy target – not necessarily just individuals, but also groups, objects, facilities, and other items of interest – or helping conceal a friendly element by determining what exactly an opponent might know. The main focus is definitely on hunting down terrorists and objects of interest, though. From the directive, the ability for special operations to quickly spot potential useful items in the field and otherwise collect vast amounts of largely physical data during operations is critical.

However, the different services each set the specific identity intelligence requirements for their own special operations forces. Each one – Army, Navy, Marine Corps, and Air Force – as well as the secretive Joint Special Operations Command (JSOC), is responsible for training its personnel in the relevant skill sets. SOCOM’s top intelligence division coordinates the actual operational aspects between the different elements and runs the central collection points for the information, but the U.S. Army Special Operations Command has the lead role in shaping the basic requirements and policies surrounding this particular mission.
The actual tasks sound a lot like something straight from an episode of a procedural crime drama on television. The document outlines six specific types of identity intelligence elite forces should be looking to gather at all times: biometric live scans, latent prints, DNA, facial images, trace materials, and documents and media. This information can be taken from individuals and sites that U.S. special operators in the course of “sensitive site exploitations” during operations, as well as from any potential person of interest, local employee, or foreign national who comes onto a facility run by elite forces at home or abroad. In the latter case, this is done to help establish those individuals as “trustworthy,” no doubt an attempt to safeguard against enemy infiltration and insider attacks, according to the directive. Officially, the guidelines require the process to adhere to any official procedures and local laws applicable to the particular situations, in order to protect individuals’ rights and privacy.

Still, the official descriptions make it clear that, if the circumstances at all allow it, elite troops are supposed to be collecting a significant amount of data. The biometric live scan, intended to be collected from living person as its name implies, sounds particularly comprehensive. The full profile includes full, rolled prints of all of the subject’s 10 fingers, scans of both of their irises, and a frontal view photograph. If “time and bandwidth are constrained” – all of this data is subsequently uploaded digitally to a central point for analysis – special operators may only take quick, flat prints and a photograph instead.


As we just mentioned, the information then goes straight into a set of larger databases and may even be checked against existing information. So, during a raid, U.S. forces can quickly check a person’s identity against watch lists of terrorist suspects. SOCOM maintains at least one “gray list,” defined as “foreign personalities of operational interest whose inclinations and attitudes toward the political and military objectives of the U.S. are unknown,” too, according to the directive. The photographs from the biometric live scans, as well as the specific facial images go into recognition databases with automated search functions.
The other intelligence doesn’t necessarily require a special operations forces locate any individuals at all. Collecting latent prints and DNA samples can help establish the presence of suspect or suspects at one or more locations, or a pattern of their movements and activities, just like they can in traditional law enforcement. “Items of interest such as bomb and drug making materiel, ignition systems, metal fragments, cups, furniture, etc, should be checked for fingerprints,” the directive notes. “DNA can be collected from anywhere.”

During a site exploitation, elite forces should grab as much trace evidence as they can, too. “Unknown substances, whether bulk, trace, solid or liquid, should be collected,” according to the official guidance. “Trace substances or materials arc easily overlooked but may be vital in linking a person to an item, location, or event. The same goes for documents and media. The U.S. Intelligence Community runs a centralized National Media Exploitation Center that provides its own, separate handbook on the exact types of items any military forces should be on the lookout to grab. Poring over cell phones, diaries, audio and video tapes, and other items – a process called Document and Media Exploitation, or DOMEX – can reveal immense amounts of information about a target.
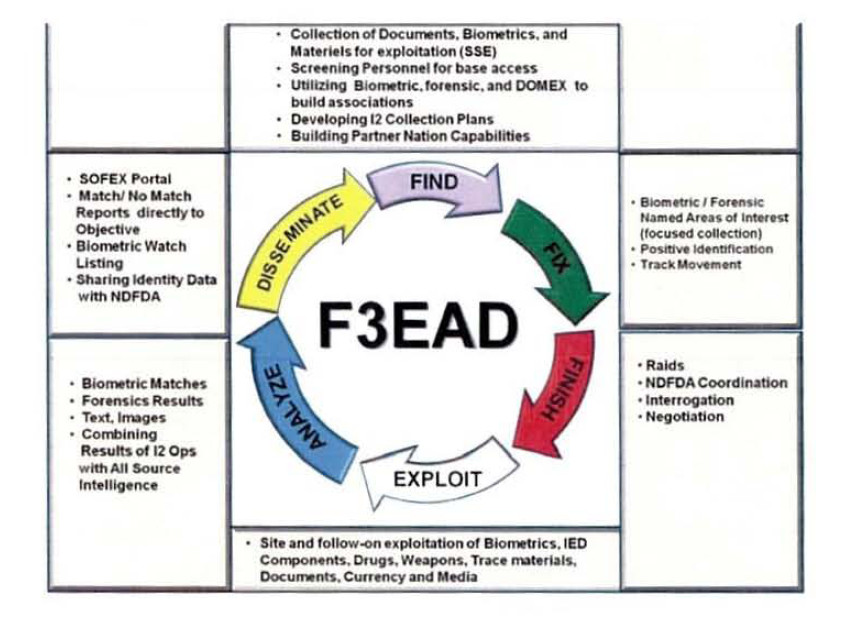
All of this information gets sent to SOCOM’s “I2 Exploitation Cell” via a network of classified and unclassified websites. You can even take a look at the relatively bland log-in page for the unclassified “identityops.com” yourself. The protected parts of the web-based network won’t show without the proper credentials installed on your computer. The system also lets SOCOM share the information with other elements of the U.S. military, as well as with the members of Intelligence Community such as the Central Intelligence Agency (CIA), National Security Agency (NSA), and Federal Bureau of Investigation, and vice versa. All of this feeds the “F3EAD” targeting cycle, which stands for “Find, Fix, Finish, Exploit, Analyze, and Disseminate.”
There is no common standard for how long information remains stored in SOCOM’s own databases, with a “forensic triage” process guiding that decision in each case. At that time, officials also determine how and when analysts can legally look at information and for how long and when and how the information gets shared with approved third parties. After analysts finally began to pick over the data, the targeting cycle would really kick in.
“If we can scoop somebody up alive, with their cell phones and diaries, it really can help speed up the demise of a terrorist group like ISIS,” Dell Dailey, a retired Army officer who once commanded JSOC and is now chairman of West Point’s Combating Terrorism Center, told The New York Times in June 2017.

We know from numerous high-profile counter-terrorism raids that identity intelligence has been important, if not essential, both before and after. After the mission that led to the death of Osama Bin Laden in May 2011, American officials used facial recognition technology and DNA testing, based on information collected at the Al Qaeda leader’s compound in Pakistan, to confirm his identity. The raiding force also scooped up all manner of computers, thumb drives and more – including an apparently extensive collection of pornography – to aid in tracking down his associates. Though the U.S. government has released some of the information it gathered at the scene, much of it remains classified as it is still apparently operationally relevant.
Other records the author obtained via the Freedom of Information Act showed that documents and media, and cell phones in particular, were key drivers of targeted strikes against insurgents in Afghanistan, at least during 2013. “SSE results = JP/TD,” an Email from a member of the Air Force’s 16th Special Operations Squadron declared, using acronyms for “sensitive site exploitation,” “jackpot,” and “touchdown.” The U.S. military uses the term “jackpot” to describe a successful strike against a particular individual, while “touchdown” refers to a an attack focused solely on a specific electronic signal, such as a particular cell phone or radio.

Since at least 2015, a JSOC element known publicly as the “Expeditionary Targeting Force” has been conduct intelligence driven operations against ISIS. That year, special operators had grabbed various physical materials during another mission in Syria that killed the terrorist group’s “emir of oil and gas” Abu Sayyaf. The elite troops did capture his wife, Umm Sayyaf, alive, and they undoubtedly processed her additional identity intelligence.
The June 2017 New York Times story also described how even though a secretive raid in Syria two months earlier had killed ISIS moneyman and fixer Abdurakhmon Uzbeki, preventing interrogators from quizzing him directly, the mission netted significant amounts of identity intelligence that could lead to additional raids. There have been other raids in both Iraq and Syria that likely used and produced similar information and it seems reasonable to assume it’s been a key part of other direct action operations against terrorists elsewhere around the world, too.
All in all, it seems that the SOCOM directive’s top assumption appears to be more of a fact. Intelligence driven operations have become the norm and identity intelligence looks set to continue being a key part of the decision-making cycle.
Contact the author: joe@thedrive.com
